Update your iPhone NOW: Apple is releasing an urgent software update – here’s how to install it on your smartphone
>
- Embarrassing bug comes four days before new iPhone announcement
- Apple had to roll out a software update at the last minute. Here’s how to get it
Just six weeks after Apple released its last software update, Apple urgently had to release a follow-up.
iOS 16.6.1, released worldwide on Thursday, fixes a security bug that makes iPhones vulnerable to “spyware”: software that steals information from a device.
Apple was alerted to the bug by the University of Toronto’s Citizen Lab, which said it is “capable of compromising iPhones without any interaction from the victim.”
In a web message about iOS 16.6.1, Apple confirmed that the new update “provides important security fixes” without providing additional details, though it did thank Citizen Lab experts “for their help.”
Apple will announce a brand new mobile operating system called iOS 17 alongside the new iPhone 15 next week.
Apple confirmed that the update “provides important security fixes” but would not confirm further details
Unfortunately, the bug is too dangerous to wait for the release of iOS 17 (expected later this month), so Apple has had to quickly roll out this latest version of 16.6.
To install the urgent update, users simply need to go to their iPhone settings and select ‘General’ followed by ‘Software Update’.
A facts window about iOS 16.6.1 should appear with the message: “This update provides important security fixes and is recommended for all users.”
Tapping ‘Download and Install’ will start the update. This may take a few minutes.
Apple said the update is also available for iPadOS, the operating system that runs on its iPads.
The tech giant said: “To protect our customers, Apple does not disclose, discuss, or confirm any security issues until an investigation has occurred and patches or releases are available.”

Apple is already expected to announce a brand new mobile operating system next week, called iOS 17, along with the new iPhone 15. But it had to quickly roll out this latest update to its current system iOS 16 due to the potential dangers of the bug
However, Citizen Lab provides many more details about the vulnerability, which is used by cybercriminals to deliver the infamous ‘Pegasus’ spyware, created by Israeli company NSO Group.
In a blog postCitizen Lab said it uses an ‘exploit chain’ method – a method that involves multiple vulnerabilities to compromise the victim step by step – but without any interaction from the victim (“zero click”).
“Citizen Lab immediately disclosed our findings to Apple and assisted in their investigation,” the research group said.
‘We expect to publish a more detailed discussion on the exploitation chain in the future.
‘We urge everyone to update their devices immediately.
“This latest discovery shows once again that civil society is being targeted by highly sophisticated exploits and for-hire spyware.”
Citizen Lab also advised any unnamed iPhone user “who may be at increased risk because of who they are or what they do” to enable Lockdown Mode, Apple’s security feature first released last year.

Citizen Lab provides many more details about the vulnerability, which is used by cybercriminals to deliver the infamous ‘Pegasus’ spyware, created by Israeli company NSO Group (file photo)
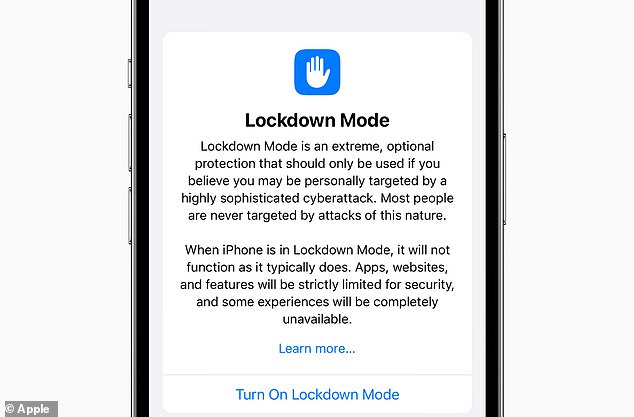
Citizen Lab also advised any iPhone user “who may be at increased risk because of who they are or what they do” to enable Lockdown Mode, Apple’s security feature first released last year.
When a device is in lock mode, apps, websites, and features are restricted for security reasons and others are completely disabled.
For example, most types of message attachments in the Messages app, except images, are blocked, and other features, such as link previews, are disabled.
Lockdown Mode is an optional protection for users who face “severe, targeted threats to their digital security,” such as journalists and activists, Apple said.
