Google is urging millions of Chrome users to update browsers NOW after discovering a flaw that could allow hackers to take over computers
- Google has released a ‘critical’ Chrome browser update in response to a software bug
- Hackers used the flaw to remotely access users’ computers
- The hackers used an HTML page to trick users into clicking on it, which opened malware
- READ MORE: Hackers publish NHS patient details after cyber attack
Google has urged millions of Chrome users to update their browsers after discovering a malicious attack that allowed hackers to take control of computers.
The tech giant warned that cybercriminals are using malicious pop-up windows or websites to gain access to an unsuspecting victim’s personal information.
A ‘critical’ update has been rolled out, closing the loophole that leaves your servers vulnerable to what’s called a ‘zero day’ attack.
The name comes from the fact that an attacker has discovered a weakness at the manufacturer, leaving zero days to fix the problem because the server has already been compromised.
The update can be accessed in Google’s Chrome browser under the “Settings” section.
Google has released a ‘critical’ Chrome update to protect users from cyber attacks
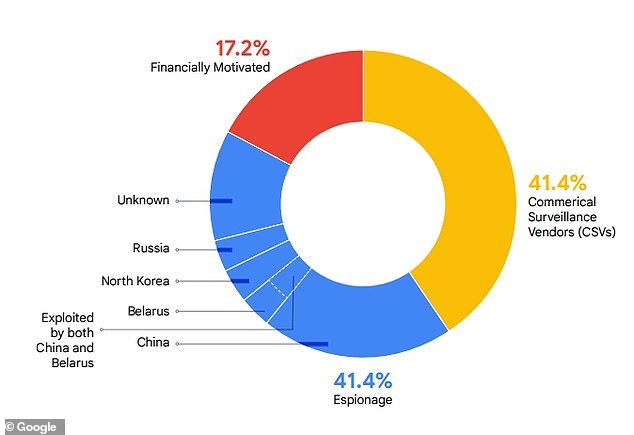
Google confirmed that Russia, North Korea, Belarus and the People’s Republic of China had caused many of the hacks
Googling reported that the flaw in all previous versions of Chrome “allowed a remote attacker to exploit heap corruption via a crafted HTML page,” but did not specify what the flaw was.
When a fake HTML page appears on the screen, it may look like a normal website, but instead, when the user clicks on it, a hacker can use remote access to take control of the person’s computer.
The HTML page may also appear as a pop-up that urges the user to download the latest antivirus software or the latest version of the browser, but instead installs software that allows actors to steal the user’s personal information.
Google advises users to continually update their browsers to the latest version to ensure all security measures are up to date.
These updates ensure that you do not have to pay for antivirus software, because the new Chrome version fixes all pre-existing vulnerabilities.
To update Chrome, users need to open the browser, click the three dots at the top right of the screen and then click ‘Settings’.

Hackers gain remote access to Chrome users’ personal data via an HTML page
There is the option to click ‘About Chrome’ on the left side, which will check for and download updates.
Google has recommended that users leave automatic updates enabled so that critical security fixes and new features are automatically added when they become available.
The update comes after a analysis from Mandiant and Google’s Threat Analysis Group found that there were 87 zero-day attacks in 2023, a 50 percent increase from the previous year.
Google reported that hackers have expanded their reach to third-party sites and libraries for maximum impact. Because these sites offer more than one product, this is a prime target for hackers to exploit Chrome’s security flaws.
“We saw this theme repeated among threat actors of all motivations, looking for vulnerabilities in products or components that provided broad access to multiple targets of their choice,” a Google spokesperson said Tech radar.
Last year, security experts warned users not to download a new version of Chrome in a browser because it could contain malicious software.
In 2023, roughly 41 percent of attacks were carried out by espionage efforts, while another 41 percent were carried out by commercial surveillance vendors and 17 percent were financially motivated, according to the analysis.
Google reported that about half of all attacks came from malicious actors in Russia, North Korea, Belarus and China, with 12 of the zero-day vulnerabilities attributed to government-backed actors from the People’s Republic of China.
“The actor showed specific interest in information of political or strategic importance to the Government of the People’s Republic of China, targeting global governments and organizations in high-priority sectors,” the analysis said.
