Warning for millions of Chrome and Safari users after Russian cyberattack
Google is urging its users to “apply patches quickly” and “keep software fully up to date” after it discovered a nine-month-old cyberattack linked to Russian spies.
Worse, this Russian espionage campaign appears to be using commercial “spyware” developed by a Greek cyber intelligence agency, which was sanctioned by the U.S. government in March of this year for “misuse of surveillance tools.”
Spyware from the company Intellexa, based on the island of Cyprus, has been involved in attacks from Ireland to Vietnam and the United States.
Fortunately, according to Google, most of the vulnerabilities exploited in this hacking operation have been patched for users who have installed important updates for Apple iOS, the Safari browser, and Google Chrome.
Google is urging its users to “quickly apply patches” after discovering a nine-month-old cyberattack it has linked to Russian spies. The tech giant said the vulnerabilities have been patched for users who have installed updates for Apple iOS, the Safari browser and Google Chrome.

Google’s Threat Analysis Group rated it with “moderate confidence” that the hacking campaigns it uncovered were linked to Russia’s Foreign Intelligence Service (SVR). Above, Vladimir Putin visits SVR headquarters in Moscow on the spy agency’s 100th anniversary
Google’s Threat Analysis Group noted in its report that the flaws that exposed iPhone and iPad users to these attacks were patched in September 2023 for anyone who updated to Apple iOS 16.7 and Safari 16.6.1.
Also for owners of Android phones and users of the Google Chrome browser, the vulnerabilities for these attacks were fixed in May 2024 with Chrome version 124.0.6367.201/.202 for Windows and macOS, and version 124.0.6367.201 for Linux.
“We notified both Apple and our partners at Android and Google Chrome about the campaigns when we discovered them,” said Clément Lecigne, a security engineer at Google.
Lecigne, who lives in Switzerland, added that Google’s threat analysis determined with “moderate confidence” that the hacking campaigns discovered in the wild “were associated with the Russian state-backed actor APT29.”
APT29, sometimes referred to as Cozy Bear or Group 100, is an evolving set of hacking and spyware tools that Western intelligence agencies have long suspected of being the work of a team of hackers acting on behalf of Russia’s SVR foreign intelligence agency.
The APT29 hacking payloads were discovered on government websites, intended for the Mongolian cabinet and foreign ministry, suggesting they were for espionage purposes.
“We also notified the Mongolian CERT (Cybersecurity Emergency Response Teams) to remediate the infected websites,” Lecigne said in his report.
However, Google cybersecurity researchers warn that there is a broader concern that this form of attack is likely to be repeated, not just by Russian state hackers, but by any well-trained team using the same spyware tools.
In a timeline published alongside the new report on the case, Google’s Threat Analysis Group noted that the key “exploits” used to turn these two Mongolian government websites into a “watering hole” trap for unsuspecting web visitors — likely officials from the Central Asian country and possibly U.S. diplomats and spies in the region — came from commercial spyware companies.
‘In each iteration of the watering hole campaigns,’ Lecigne’s report noted‘The attackers used exploits that were identical or remarkably similar to exploits from CSVs (commercial surveillance software vendors) Intellexa and NSO Group.’
Since November 2021, the Biden administration has blacklisted the spyware company NSO Group from the US Department of Commerce, prohibiting US companies from doing business with the Israeli organization.
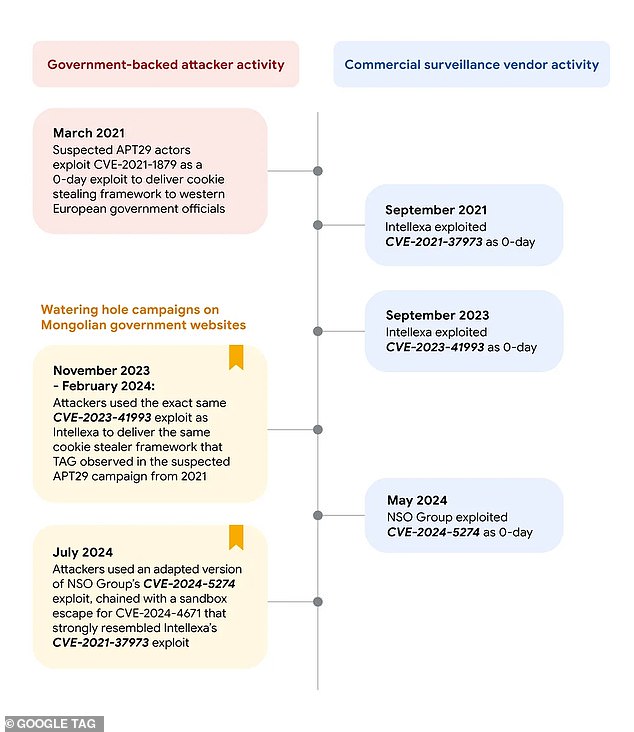
In a timeline published alongside their new report, Google’s Threat Analysis Group noted that the key exploits used to turn two Mongolian government websites into a “watering hole” trap for unsuspecting web visitors came from two U.S.-sanctioned spyware companies.

One such company, Intellexa, was sanctioned in March 2019 for its Predator tool, which allows hackers to infiltrate devices via stunning “zero-click” attacks that require no user interaction.
The White House accused NSO of allowing its patented Pegasus software “to be misused around the world to facilitate human rights violations, including to target journalists, human rights activists and others perceived as dissidents and critics.”
Intellexa received a similar penalty for its Predator tool, which allows hackers to infiltrate devices via stunning “zero-click” attacks that require no user interaction.
Google’s security team was alarmed to see suspected Russian state actors taking advantage of already patched security vulnerabilities via commercial spyware packages.
The campaign clearly implied that spies hoped to infiltrate as many Mongolian government officials and visiting foreign diplomats as possible, counting on individuals not updating their personal web browser software.
Older patched vulnerabilities, called n-day exploits, are generally considered less dangerous than brand new, unpatched vulnerabilities, called 0-day exploits.
“We don’t know how the attackers got these exploits,” Lecigne warned.
“What is clear,” he noted, “is that APT actors are leveraging n-day exploits that were originally used by CSVs as 0-days.”
