Urgent warning to Google users after cyberattack targets search browser with fake ads – here’s how to stay safe
Cybersecurity experts are urgently warning Google users of an attack that may have obtained their personal data.
Hackers bought sponsored ad space directly from the company, posing as the tech giant’s real Google Authenticator site, which offers users two-factor password security.
The scam campaign used what appeared to be a legitimate Google URL, but upon closer inspection it contained terms the company would not typically use.
Users who downloaded the fraudulent link may have given hackers access to their bank account details, address and personal IP address.
Experts are now urging victims to: Download and run a virus scanner immediately, change all passwords and delete all temporary files.
Hackers bought sponsored ad space directly from the company, posing as a real Google Authenticator site that offers users two-factor password protection
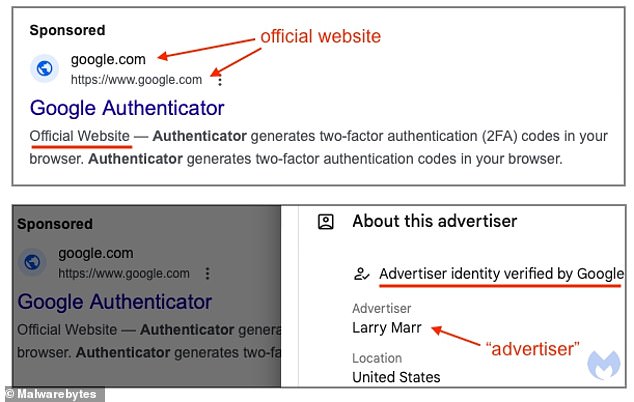
The new ad campaign, found by anti-malware software company Malwarebytes, featured a Google.com URL link that had previously been a sign of assurance that the site was legitimate
Experts previously advised users to only click on advertising links that have a Google domain, but hackers appear to have taken this advice, using text modifiers and cloaking technology to mimic official sites.
The malicious ad lured users into downloading convincing authenticator clones installed by a malware distribution campaign called DeerStealer, which claimed that its developer, Larry Marr, had been verified by Google.
“The truth is that Larry Marr has nothing to do with Google and is probably a fake account,” Malwarebytes researcher Jérôme Segura, who discovered the cyberattack, said in a blog post.
“We can track what happens when you click on the ad by monitoring web traffic. We see a number of redirects through intermediate domains controlled by the attacker, before we end up on a fake Authenticator site.”
According to Malwarebytes, users who searched for Google products in their browsers saw the ad as sponsored and clicked on it without hesitation.
They were then redirected multiple times until they ended up on a fake site hosted on the developer platform GitHub.
The researchers also found that after clicking the ‘download’ button, users received a pop-up named Authenticator.exe, which downloaded the malware onto their computer.
Google Authenticator provides multi-factor authentication services that add a second layer of security to Google Accounts by requiring a time-based one-time password in addition to the user’s normal password.
According to a report from Google, nearly four million people have downloaded Google’s legitimate authentication service since October 2022. Statistics.
Google told DailyMail.com that attackers such as DeerStealer created thousands of accounts to evade detection while modifying the URL and site text and using cloaking software to show Google reviewers different websites and information than users see.
If the fraudulent authenticator is successfully downloaded, DeerStealer will have access to your sensitive information, including addresses, passwords and banking details, identity theft and the victim’s IP address.
“We have to keep in mind that Google Authenticator is a well-known and trusted multi-factor authentication tool, so it is ironic that potential victims are being compromised while trying to improve their security,” Segura said.
‘We recommend that you do not click on advertisements to download software. Instead, go directly to the official repositories.’
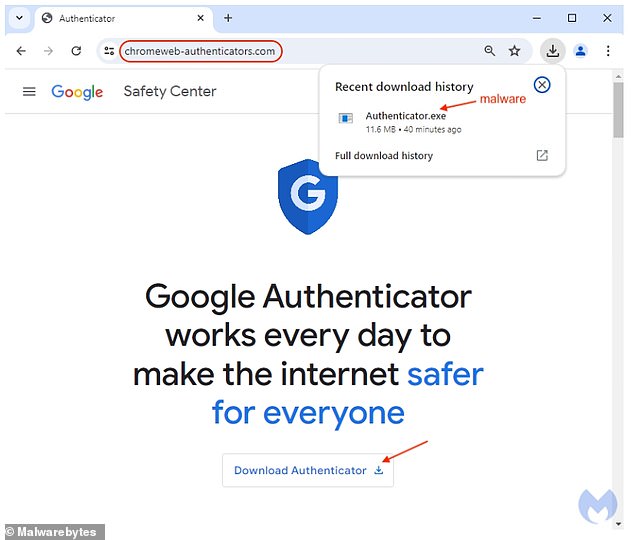
After users clicked the ‘download’ button, they were presented with a pop-up named Authenticator.exe that downloaded the malware onto their computer
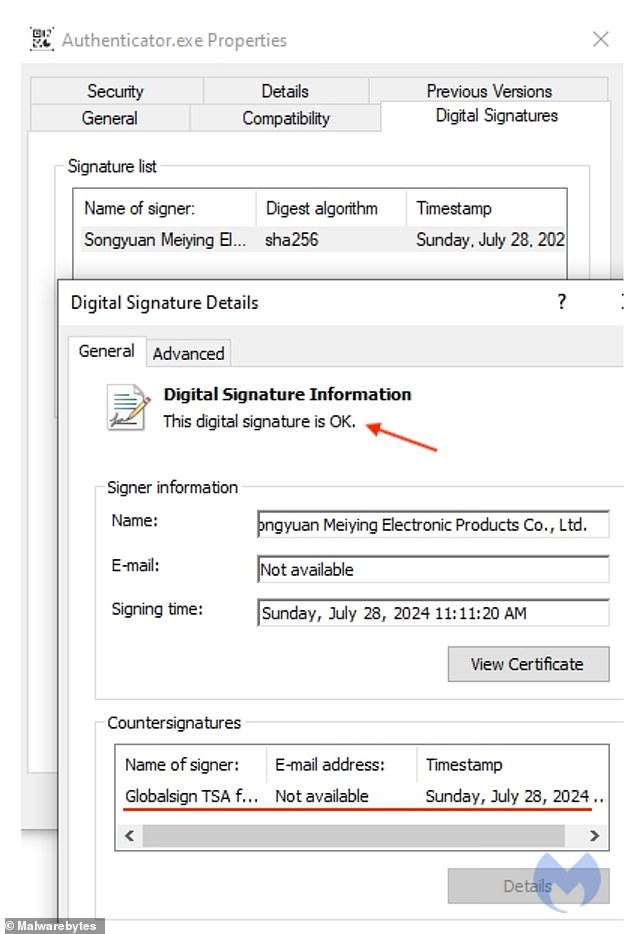
The malware was verified by Google reviewers who did not mark it as a fraudulent link
Google has not disclosed when the malware was first posted or how many people were affected.
The company told DailyMail.com that the sponsored authenticator link was removed on July 30 after anti-malware software company Malwarebytes alerted them to the fraudulent activity.
“We prohibit ads that attempt to evade our enforcement by hiding the advertiser’s identity to mislead users and spread malware,” a Google spokesperson said.
“When we identify ads that violate our policies, we remove them and suspend the associated advertiser account as quickly as possible, as we did in this case.”
However, people who downloaded the fraudulent link are still at risk.
Google said it is still investigating the issue and is expanding its automated systems and human reviewers to identify and remove malicious campaigns.
While it’s difficult to tell the difference between a DeerStealer link that convincingly claims to be a “Google-Verified Advertiser Identity,” users should pay attention to the suspicious URL – chromeweb-authenticators.com – that only appears right before the Authenticator.exe file is downloaded.
However, the only way users can protect themselves is to avoid clicking on sponsored links and instead scroll down to find legitimate web resources.
