One of the most popular text editors around has been infected with malicious ads
A new malicious Google ad campaign that was active for “months” has likely halted the deployment of Cobalt Strike on unsuspecting victims, researchers have warned.
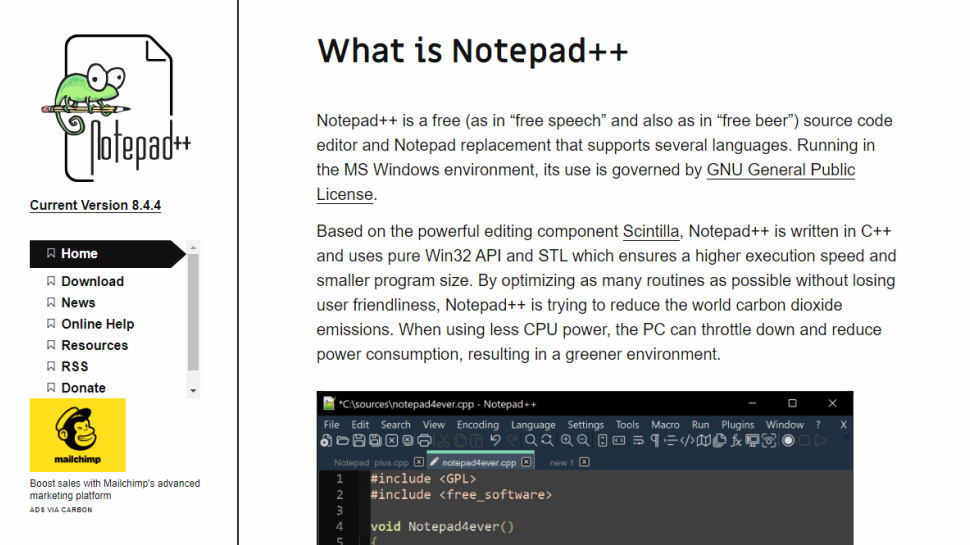
Cybersecurity researchers at Malwarebytes recently discovered a campaign that hijacked Google Ads and served them to people searching for Notepad++, a popular word processing software.
When someone searches for Notepad++ (or types a similar query that should open the editor), the first few results they see are advertisements, some of which take them to a malicious site.
Cobalt attack
This is a popular tactic that has been seen before. On the search engine results page, the site titles are displayed in larger font than the links, which can make it easy for people to forget to double-check the site and simply click on the suggested result. Furthermore, Google is generally considered a trusted, safe environment, where people do not question the motives of the sites that appear there (especially on page one).
Either way, once the victim clicks on the link, the site first runs a few quick tests to make sure the visitor is real (and not a bot, a VPN, or the like) and then displays a site that looks almost identical to the website. legitimate Notepad++ site. For those deemed bots (or otherwise unsuitable visitors), the site redirects them to a decoy site. Regular customers will see a 404 page.
Malwarebytes was inactive at the time of the analysis and could not investigate the actual payload, but the researchers speculate that the attackers most likely used Cobalt Strike. This tool often precedes the deployment of ransomware, BleepingComputer reports.
Abuse of ad networks is nothing new. Cybersecurity experts warn users to be careful about what they do online, and always double-check that they are downloading legitimate software from legitimate sources. Illegal software and software distributed via links in emails and social media posts are almost always malicious.
